
Company Overview
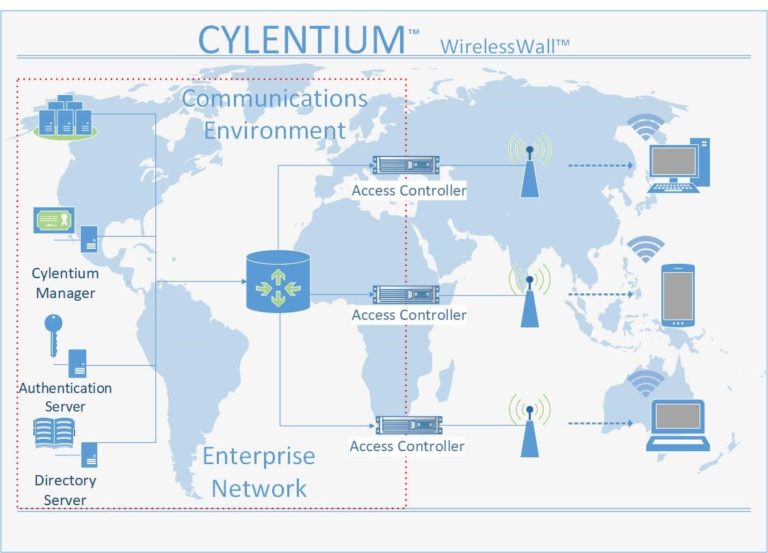
Cylentium is a cyber security company that provides military grade Intelligence Protection Networks (IPNs), Enterprise Protection Networks (EPNs), and Personal Protection Networks (PPNs) through wireless and ethernet cloaking and bubble technologies. By creating an invisible environment, Cylentium cloaks and removes you from the threat surface and vectors.
Cylentium is a cyber security company that provides military grade Intelligence Protection Networks (IPNs), Enterprise Protection Networks (EPNs), and Personal Protection Networks (PPNs) through wireless and ethernet cloaking and bubble technologies. By creating an invisible environment, Cylentium cloaks and removes you from the threat surface and vectors.
Zero Identity
Zero Identity is the cyber term used to represent Invisibility Cloaking Bubble Technology (ICBT).
Zero Identity is the process of making invisible to detection, military grade Intelligence Protection Networks (IPNs), Enterprise Protection Networks (EPNs), and Personal Protection Networks (PPNs), wireless and ethernet systems, and communication systems, invisible and non-detectable through cloaking and bubble technologies. By creating an environment of invisibility, Zero Identity cloaks and removes all protected assets and targets from the threat surface and vectors by making them invisible. If a threat actor, or hacker, cannot see or identify a target, said target in theory, through non-detectability, becomes non-hackable or penetrable.
The starting premise is, in today’s world, we know hackers can always see, identify, and determine potential attack prospect. Accepting and understanding that if you can be seen and identified, then it stands the associated cyber risk vulnerability quotient of being selected is greater than Zero. If you cannot be seen or identified, the hypothesis is the associated cyber risk vulnerability quotient is Zero. If you can not see me, you do not know about me; therefore, the correlating probability of being chosen is Zero.
This new condition of Zero Identity changes the overall cyber risk environment. Injecting or changing the mathematical calculation with the insertion of a Zero Probability because of Zero Identity, changes the overall risk calculation. Cyber economics and risk analysis will need new computations, algorithms, and methodologies to adapt to Zero Identity.
Cylentium Team
Passionate about The Future & Technology Innovation



Wayne Ronhaar
CEO
Rob Langhorne
CTO
Ian Ross
CRO
Chief Executive Officer
Chief Technology Officer
Chief Compliance Officer
Board Advisor
Join Our Team
There are many variations of passages of Lorem Ipsum available, but the majority have suffered alteration in some form, by injected humour, or randomised words which don’t look even slightly believable. If you are going to use a passage of Lorem Ipsum, you need to be sure there isn’t anything embarrassing hidden in the middle of text.
EMAIL US YOUR RESUME
SEE JOB POSTINGS
Need more information?
We are here to help. Contact us by phone or email.
